360° Technology Due Diligence
Deeper, faster insights into the tech
Through a unique combination of code scanners and expert analysis, we identify risks, technical debt and upside potential, delivering investor-ready recommendations that drive tangible long-term technology value creation.
A data-driven approach to unlocking value in tech investments
Vaultinum equips private equity investors with a clear, data-driven evaluation of a tech asset’s risks and upside potential, addressing key investment concerns.
Risk exposure
Identifying hidden vulnerabilities, obsolescence risks, and structural weaknesses that may affect valuation.
Cost impact
Quantifying remediation costs (CapEx/OpEx) and assessing the feasibility and impact of mitigation strategies.
Scalability and integration
Evaluating whether the technology can support growth, integrate post-acquisition, and align with future expansion plans.
Operational efficiencies
Uncovering cost-saving opportunities, performance optimisations, and EBITDA-enhancing strategies.
A unique combination of tools, data and experts
Comprehensive IT Due Diligence analysis
Vaultinum conducts a multi-dimensional assessment to provide a holistic view of technology, including its impact on human capital and financial performance.
Infrastructure scalability
- Enterprise or Saas
- Architecture
- Build up readiness
Software scalability
- Technical debt
- SDLC Assessment
- Team Performance
Cybersecurity
- Cyber-readiness
- Code vulnerabilies
- Network footprint
Open Source
- OSS inventory
- IP Risks in Git History
- Licence compliance
Data value chain
- Data collection
- Data usage
- Data value
FinOps
- Cloud cost optimisation
- IT cost efficiency
- Alignment with growth strategy
AI maturity
- Maturity of the model
- Complexity of the model
- Optimisation and accuracy
AI disruption
- Impact of AI players
- AI as an enabler
They trust our expertise
Our Technology Due Diligence clients
Our Due Diligence approach
A seamless, data-driven tech due diligence process to go deeper, faster.
01
Online assessment
02
Source code scan and network footprint
03
Dataroom & expert review
04
Tech Due Diligence investor report
01
Online assessment to evaluate processes and governance
- Cybersecurity posture
- Software development and IT infrastructure
- Third party software IP compliance
- Data privacy
- AI maturity
- Product roadmap
The online platform delivers rapid insights by benchmarking scores against industry standards, identifying opportunities and vulnerabilities, and generating a report with clear guidelines and recommendations.
02
Source code scan & network footprint
We gather insights from multiple scanners and dataroom documentation, assessing:
- Cyber vulnerabilities (CVE, CWE)
- Public information
- Software scalability
- Infrastructure scalability
- Code hygiene and maturity
- Open Source dependencies
Optional add-ons include penetration testing and FinOps evaluation.
03
Dataroom and expert review
Contextualisation interviews with our subject matter experts to:
- Identify mitigating factors and risk reduction strategies
- Analyse security, compliance, and long-term operational risks
- Assess the technology environment, scalability, and integration feasibility
- Evaluate technical debt
- Identify the upsides of the tech and roadmap
- Align findings with business objectives
04
Tech Due Diligence investor report
A comprehensive risk report and action plan highlighting both downside exposures and upside levers through analysis of:
- Tech scalability, cloud readiness, and stack efficiency
- Team performance and leadership
- Cyber risks and open-source compliance issues
- Technical debt with OPEX/CAPEX impact projections
- Overall tech-related value erosion risks and optimisation potential
Evaluating team dynamics and development processes
A strong development team is a key driver of technology scalability and long-term value creation. Vaultinum’s Tech Due Diligence goes beyond assessing technical architecture to provide insights into how the developper team operates, its stability, and its efficiency.
Tracking team size and evolution over time
We examine whether the number of developers aligns with codebase growth. A mismatch may indicate inefficiencies or technical debt accumulation
Measuring developer turnover and key person risk
Frequent departures can disrupt projects and create knowledge gaps. We track team changes to highlight retention risks and dependencies on key individuals.
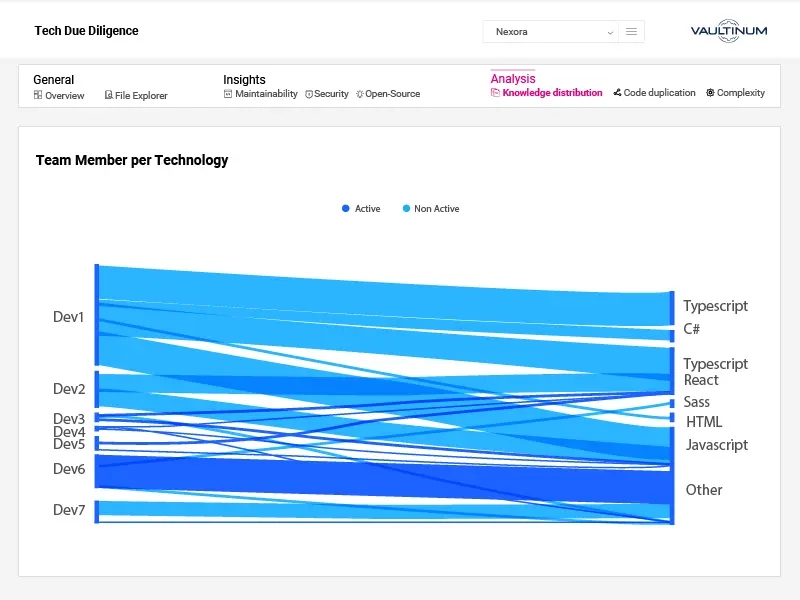
Assessing knowledge distribution across projects and technologies
Reliance on a few developers can create operational risks. We assess how expertise is spread across the team to identify potential bottlenecks.
Analysing individual developer contributions
Commit frequency provides a first-level insight into workload balance and development efficiency, helping to detect disparities and process inefficiencies.
All-in-one platform for tech performance monitoring
Vaultinum’s platform centralises all data relevant to tech due diligence, enabling fund managers to securely access and monitor KPIs post-Tech Due Diligence.
Secure dataroom for confidential document management
Access to online assessments for continuous monitoring
Secure code upload
Detailed code analysis reports
Investor-focused Technology Due Diligence reports
Portfolio view and dashboard for comprehensive performance insights
Innovating Due Diligence
At Vaultinum, we understand the risks associated with tech investments. Our mission is to help investors dare with care.
Our unique approach to technology due diligence combines advanced tools, expert insights, and comprehensive data to deliver deep, actionable analysis faster. This integrated method provides multi-dimensional risk assessments, driving technological optimisation and long-term value creation. By leveraging these insights, investors can enhance EBITDA and unlock growth potential through strategic tech synergies.
Our team is there to turn tech risks into financial metrics and show you how to maximise potential and grow EBITDA through tech.

How to run an IT audit without access to source code ?
Whether you are in the pre-deal phase or the target is unable or unwilling to upload its code, Vaultinum provides the insights you need.
Red flag report
- High-level risk analysis with or without a code scan
- Identification of critical risks and vulnerabilities
- Profiling based on non-intrusive analysis
Docker Code analysis
- Keeps code private by running locally
- Deploys easily on compatible infrastructure
- Provides essential insights
Dare with care
Beyond Tech Due Diligence: completing the risk picture
In addition to our core tech due diligence services, we offer specialised audits that enhance and complete the technology assessment.
Data Privacy Compliance
Evaluates data management practices within the target company and provides operational recommendations on governance and compliance processes.
Intellectual Property Research
Conducts a comprehensive IP assessment beyond third-party software, including trademark and domain name coverage, patent checks, and IP governance.
ESG analysis
Leverages our automated ESG questionnaire, developed with industry experts, to deliver a scored report with industry benchmarks, supporting responsible investment decisions.
Network Footprint Analysis
Network Footprint Analysis: Utilises a non-intrusive reconnaissance process to evaluate the cybersecurity health of the target company from an external perspective, serving as the first step in identifying cyber vulnerabilities.
We provide a complete picture, combining in-depth analysis with clear business insights to ensure investors understand both the risks and the value creation potential of the tech asset.”
Philippe Thomas, CEO of Vaultinum
Trusted by investors and tech leaders
Tech Due Diligence Checklist
Key questions you don’t want to miss when performing a Tech Due Diligence
FAQ about Tech Due Diligence
What is Technology Due Diligence (TDD)?
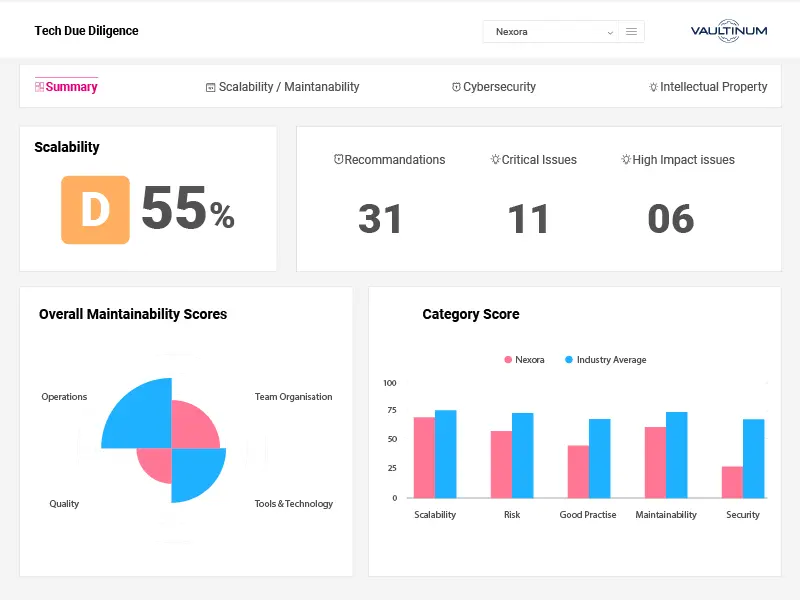
Technology due diligence is a structured evaluation of a company’s technology assets, architecture, and engineering capabilities, typically performed during a financing, acquisition, or strategic partnership. It aims to validate whether the technology can support the business plan, scale with growth, and withstand scrutiny from a risk, operational, and IP perspective. The process covers areas such as software architecture, codebase health, scalability, cybersecurity, infrastructure, team structure, development processes, and use of third-party or open source components. For technology-driven businesses, this audit is essential as it helps investors understand the technical foundations of the company, identify potential risks early, and assess whether future investment in the tech stack is likely to be defensive or value-accretive.
What types of vulnerabilities does the Tech Due Diligence code scan identify?
A code scan performed during Technology Due Diligence (TDD) identifies a wide range of software vulnerabilities and risk factors across three core dimensions: security, quality, and intellectual property (IP). On the security side, it can uncover known CVEs (Common Vulnerabilities and Exposures) in third-party dependencies, unsafe coding patterns, hardcoded credentials, and misconfigured encryption. From a quality and maintainability standpoint, the scan detects code complexity, dead code, duplication, and architectural anti-patterns that may hinder scalability or increase technical debt. On the IP front, it flags any use of open source components with restrictive licenses (e.g., GPL, AGPL) or unclear provenance which is essential for identifying potential compliance issues or contamination risks. These insights help investors assess the long-term viability, maintainability, and legal safety of the software asset.
How long does a Technology Due Diligence audit take?
The duration of a technology due diligence depends on the scope and complexity of the company being reviewed including the number of products, size of the engineering team, tech stack maturity, and availability of documentation and access. For a single-product SaaS company with well-organised materials, the process can typically be completed in 2 to 3 weeks. For multi-product platforms, companies with legacy systems, or where the codebase is large and less documented, it may extend to 4 weeks or more. Vaultinum works efficiently by combining structured data collection, automated code and infrastructure scans, and focused expert interviews allowing us to deliver detailed findings on tight deal timelines, while maintaining the depth and precision required for informed decision-making.
When should a Tech Due Diligence be conducted?
Technology Due Diligence (TDD) should be conducted before a transaction enters exclusivity, ideally during the confirmatory or advanced stages of a deal, once there is clear intent but before final terms are agreed. For investors or acquirers, this timing ensures technical risks are identified and factored into valuation, deal structure, or integration planning. For strategic partnerships or minority investments, a TDD may be conducted earlier to validate the strength of the tech platform before deeper commercial alignment. Delaying TDD too long can compress timelines and reduce the ability to act on findings. Starting early allows for a more thoughtful assessment of scalability, security, IP exposure, and the level of investment likely needed post-deal.
Why is Technology Due Diligence important in M&A transactions?
In M&A transactions, Technology Due Diligence (TDD) is important for validating that the target’s technology can support the investment thesis. It helps identify technical debt, scalability limitations, cybersecurity risks, and IP issues that could impact integration, post-deal investment needs, or long-term value creation. For acquirers, TDD provides clarity on whether the product is defensible, maintainable, and aligned with business objectives or whether it will require significant refactoring. It also verifies ownership and compliance of key software components, particularly open source usage. In short, TDD protects against costly surprises post-close and enables more informed deal structuring, especially in tech-heavy or software-led acquisitions.
How does Technology Due Diligence support post-acquisition integration?
Technology Due Diligence lays the groundwork for successful post-acquisition integration by identifying technical, organisational, and process-level considerations before the deal closes. It surfaces potential challenges such as incompatible architectures, infrastructure inefficiencies, fragile deployment processes, or siloed knowledge, all of which can impact how quickly the acquired technology can be scaled, maintained, or integrated into the buyer’s existing ecosystem. TDD also helps define early priorities for tech team alignment, resource allocation, and roadmap rationalisation. By clarifying what will need to change and what is already working, it enables more realistic integration planning, reduces execution risk, and accelerates time-to-synergy. For buyers with a platform strategy, it ensures the acquisition complements rather than complicates the broader tech landscape.
Our latest articles on