Global trends in Cyber Risk
Digital technologies ranging from artificial intelligence and the Internet of Things to data availability and blockchain continue to evolve at breakneck speed. Not to be outpaced, cyber risks are evolving even faster. The global cost of cybercrime in 2020 reached $945 billion, nearly double the 2016 figures.[1] According to the research organization Cybersecurity Ventures, global cost is expected to grow by 15% annually, reaching $10.5 trillion per year by 2025.[2]
Companies must prepare for the new challenges brought about by the evolving targets, techniques and impacts of cyber crimes. This article will focus on the growing risks related to: the increase in ransomware incidents, the prospect of more disruptive and expensive business interruptions, the consequences of more robust regulation and litigation risks, the pervasive theft of intellectual property, as well as new impediments to successful mergers and acquisitions.
Ransomware on the rise
The scale and scope of ransomware attacks are increasing at an unprecedented rate. This is due to a combination of factors including the rapid rise of digitalization, growing use of cryptocurrencies, increased geo-political tensions, the extraordinary environment created by the pandemic, and improved schemes which have made ransomware even more profitable.
Ransomware is a malware that infects computer devices and can lock down access to entire computer networks, effectively holding a business hostage until a ransom is paid.
The malware often infiltrates a system’s servers by means of an innocuous email (‘phishing’) sent to an employee of the targeted company. The human layer is often the weakest link in cyber defense and is thus a ripe target for cyber criminals. It is estimated that anywhere between 50% and 90% of data breaches are caused or abetted by employees.[3]
The price of ransom is growing alongside the rise in use of ransomware. The average ransom paid by companies based in Europe, the US and Canada nearly tripled from $115,123 to $312,493 in just over a year.[4] This increase is due, in part, to new tactics employed by the cyber hackers that combines data captivity with threats to leak the data on public sites, a dual threat that leaves businesses with little to no recourse but to pay the ransom.[5]
It is also due in part to the shifting of targets. Rather than targeting individual personal computers, cyber criminals are targeting public and private sector organizations of various size which enables an increase in both the ransom requested and the probability of successful payment.[6]
The threat of a ransomware attack is forecasted to only get worse with the growing use of the “franchise” model adopted by cyber criminals, whereby malware is leased on the dark net to so-called affiliates in a ransomware-as-a-service scheme with the lessors earning a royalty, thus making sophisticated ransomware more widely available and profitable.[7]
Business disruption
Whether or not a cyber incident leads to a ransom payment, the costs associated with any resulting business disruption far exceeds the amount demanded. In fact, these costs can be anywhere from five to 100 times greater than the cost of a ransom itself, often inciting businesses to pay the ransom just to avoid the costs of disruption.[8]
Business disruption is the income lost when a resource cannot be used or a service cannot be provided leading to lost sales, reduced efficiency, increased spending related to the cyber incident (recovery of IT systems, damages paid out to clients, etc.) and reputational damage.
While larger companies are usually better positioned to sustain the losses brought on by business disruption, it is small to medium enterprises (SMEs) that suffer disproportionately when they find themselves the victims of a cyber attack.
It is estimated that 45% of online attacks target SMEs.[9] Unlike larger companies, SMEs have limited or even non-existent cyber defenses or hygiene. For businesses of all sizes, the average cost of disruption is around $200,00o; for SMEs this cost can be insurmountable, with 60% of SMEs going out of business after being victimized.[10]
As for paying a ransom to avoid the costs of business disruption - paying doesn’t guarantee full recovery and it certainly doesn’t eliminate all the business disruption costs associated with ensuring that every machine is infection free. Moreover, the payment of ransom does not guarantee that a company’s data will be returned whole. The cybersecurity firm Sophos found that ransom-payers got back only 65% of the encrypted data on average, leaving more than a third inaccessible.[11] And even if the data is returned, there is no guarantee that it has not been copied for future use, sale and/or blackmail.
While many businesses rely on business interruption and property insurance to help offset the costs of cyber incidents, increasingly insurance companies are relying on the “act of war” clauses to shield them from payouts. The high profile NotPetya ransomware attack and the resulting lawsuit against Zurich American Insurance for its denial of coverage under it’s ‘act of war’ exclusion policy demonstrates that cyber insurance cannot be considered a replacement for cyber security.[12]
Increased liability
In addition to the risks related to business disruptions and ransom payments, companies also are confronted with increasing potential liability if they are found to not have complied with the laws and regulations in force in the countries in which they operate or if they are found to have been negligent, not exercising due care to limit cyber risk.
In Europe, the General Data Protection Regulation (GDPR) implements fines for businesses if they do not follow data protection guidelines or data breach reporting requirements. Businesses risk being fined, the greater of, up to 4% of their annual global revenue or 20 million Euros if they violate the regulation.[13]
The implementation of the GDPR has already led to an increase in claims notifications. According to the law firm Pinsent Manson, between March 2019 and May 2020, a total of 190 GDPR fines were issued by European data protection authorities, with a value of almost $500 million.[14] Notable large fines for violations include $57 million for Google in France and $41 million for H&M Germany.[15]
From Europe, to the US, and to the world over, data privacy regulations and mandatory breach disclosure laws vary widely, making legal due diligence across markets essential for businesses, and in particular, multinationals. The hotel group Marriott and credit score agency Equifax suffered highly publicized data breaches in 2018 and 2017 respectively, and were subject to numerous lawsuits and regulatory actions in multiple jurisdictions with Marriott facing a $130 million fine in the UK alone for the breach.[16]
Intellectual property theft
Given the pervasiveness of data breaches, companies are treating them more and more as another cost of doing business. This, however, is not at all the case with data theft concerning intellectual property (IP), which is seen as one of the greatest threats companies yet face.
While the theft of IP has been around as long as IP itself, the latest developments in cyber espionage and theft should have companies worried.
Cyber hackers are increasingly relying on Advanced Persistent Threats (APTs), where access to a system can remain undetected for an extended period of time with the goal of stealing data or penetrating a network. APT attacks are often intended to steal sensitive intellectual property or data for political or economic gains.[17]
In the early months of the pandemic, hackers targeted the World Health Organization by infiltrating its networks with the APT known as ‘Dark Hotel’; an effort to steal sensitive information relating to Covid-19.[18] The health care industry and more recently, vaccine research, are highly targeted because ultimately their IP is highly valued.
Yet, in some cases the theft of IP is meant to steal a competitive advantage, hijack new technology and trade secrets and cause hundreds of millions of dollars in R&D investments to be lost. This was the case for chip-maker AMD, where attackers stole and leaked the Xbox Series X graphics source code.
In all cases, the impact on revenue streams from IP theft by cyber intrusions may lead to reduced R&D efforts and an increase in the cost of capital if the IP is seen by investors as not sufficiently protected.[19]
Risks to mergers & acquisitions
Mergers and Acquisitions (M&A) are fertile ground for cyber criminals providing them with both short and long term opportunities.
In the short term, with business operations in transition, data is more vulnerable and at higher risk of being targeted. In the long term, M&A transactions serve as a prime opportunity to infiltrate the merging or acquired company’s networks, often by the employ of APTs, in an effort to ultimately gain access to the targeted company’s environment and information over an extended period of time.
The threats facing M&A highlights the importance of conducting cyber due diligence at the pre-acquisition phase. Indeed, more than 50 percent of companies surveyed by IBM wait until due diligence is completed before they perform cybersecurity assessments of M&A transactions.[20]
While a company may have state of the art cyber security, if it acquires a company with weak security or existing vulnerabilities it could be liable for any damage from incidents that occurred prior to the merger, as seen in the data breach of the hotel group Marriott.Although the data breach was discovered in 2018, it was traced to a cyber intrusion that occurred in 2014 at Starwood, a hotel group that it acquired in 2016.[21] Had Marriot conducted cyber due diligence during pre-acquisition, this vulnerability could have been discovered and/or measures could have been taken together with a revised valuation.Further, acquiring a company that may have vulnerabilities may amount to integrating a trojan horse.
Building cyber resilience: Know Your Software
Despite these challenges and the fact that being a victim of cyber crime is becoming more a question of when rather than if, most organizations do not have a plan in place to both prevent and respond to cyber security breaches.[22]
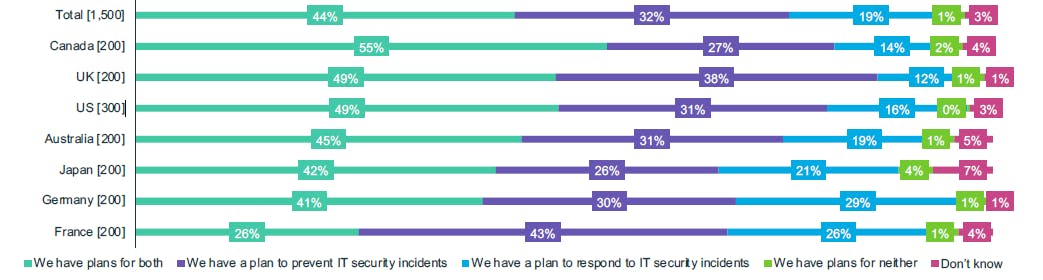
Figure 1. Proportion of organizations that have a plan to prevent and respond to IT security incidents. Source: McAfee, “The Hidden Costs of Cyber crime”
The importance of having a solid cyber risk management program cannot be underestimated. Every day new technical and security breaches are discovered. Every business change can create unintended vulnerabilities. Every new employee, consultant or contractor is a new risk that needs to be managed. A hacker only needs to be successful once, while a company’s security measures must be successful 100% of the time - in an ever-changing threat landscape. The regular undertaking of cyber security audits, evaluating their results and researching and implementing improvements is thus an essential, and never-ending, process that should be adopted by all organizations that take cyber risk seriously.
Vaultinum, a Swiss based digital solutions company, has developed an intelligent auditing tool that enables companies to conduct their own due diligence in cybersecurity, examining an organization’s security risk management program, data protection procedures, security certifications, and office, equipment and infrastructure protections. The Know Your Software solution is a self-assessment questionnaire developed by leading experts in cyber security with the aim of helping companies improve their cybersecurity awareness, mitigate risks and put in place recommended policies and procedures based on industry standards in order to help prevent cyber incidents from occurring and building resilience in the face of one.
References:
[1] Smith, Z.M., Lostra, E., Lewis, J.A. (2020). The Hidden Costs of Cybercrime. McAfee.
[2] Morgan, Steve. “Cybercrime To Cost The World $10.5 Trillion Annually By 2025”. Cybercrime Magazine, 13 Nov. 2020
[3] Dobie, G., Whitehead, J. (2020). Managing the impact of increasing interconnectivity: Trends in Cyber Risk. Allianz Global Corporate & Specialty.
[4] Sroxton, Alex. “Average ransomware cost triples, says report”. Computer Weekly.com, 17 Mar. 2021
[5] Singleton, C. (2021). X Force Threat Intelligence Index 2021. IBM Corporation.
[6] (2020). Internet Organized Crime Threat Assessment 2020. Europol.
[7] Morgan, Steve. “Cybercrime To Cost The World $10.5 Trillion Annually By 2025”. Cybercrime Magazine, 13 Nov. 2020
[8] Riley, Tonya. “The Cybersecurity 202: Global losses from cybercrime skyrocketed to nearly $1 trillion in 2020, new report finds”. Washington Post, 7 Dec. 2020
[9] Steinberg, Scott. “Cyberattacks now cost companies $200,000 on average, putting many out of business”. CNBC, 13 Oct. 2019
[10] Steinberg, Scott. “Cyberattacks now cost companies $200,000 on average, putting many out of business”. CNBC, 13 Oct. 2019
[11] Bajak, Frank. “Ransomware gets paid off as officials struggle for fix”. Associated Press, 22 June 2021
[12] Garrie, Daniel; Rosen, Peter. “'Act Of War' Questions In Cyberattack Insurance Case”. Law 360, 23 April 2019
[13] EU General Data Protection Regulation (GDPR): Article 83, Section 6.
[14] Dobie, G., Whitehead, J. (2020). Managing the impact of increasing interconnectivity: Trends in Cyber Risk. Allianz Global Corporate & Specialty.
[15] Idem
[16] Dobie, G., Whitehead, J. (2020). Managing the impact of increasing interconnectivity: Trends in Cyber Risk. Allianz Global Corporate & Specialty.
[17] Adam, M. “Cyber Risk in a new era: insurers can be part of the solution”. S&P Global Ratings, 2 Sep 2020
[18] Seals, T. “Hackers amp up Covid-19 IP Theft Attacks”. Threat Post, 28 Dec 2020
[19] Smith, Z.M., Lostra, E., Lewis, J.A. (2020). The Hidden Costs of Cybercrime. Center for Strategic and International Studies.
[20] Idem.
[21] Brewster, T. “Revealed: Marriott's 500 Million Hack Came After A String Of Security Breaches”. Forbes, 3 Dec. 2018
[22] Smith, Z.M., Lostra, E., Lewis, J.A. (2020). The Hidden Costs of Cybercrime. McAfee.

Recommended for you


